CYBER SAFETY
India houses the world’s second largest Internet population. With greater reliance on our laptops and phones and the daily consumption of the Internet increasing day by day, inevitably it leaves us vulnerable to various threats within cyberspace. While information technology has its perks, it also has its share of banes. Although most of us are aware of the moral weight of certain acts on the Internet, such as making slanderous remarks or sharing obscene content within groups, the existence of legal remedies and the process of registering a complaint in relation to this are not of common knowledge.
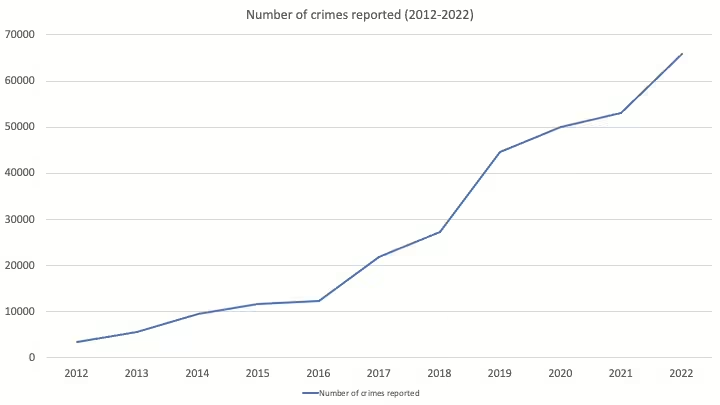
Cyber abuse includes financial, personal, institutional and even terrorist strikes. We will be focusing on online safety in personal space. Some of the commonly found cyber safety issues are:
- Unsolicited communication: These could be unwelcome sexual requests, comments, videos, pictures, text, voice, calls or any other form of communication with a sexually offensive nature sent to you without your consent or knowledge repeatedly.
- Threats: This is when you or your loved ones are threatened with physical harm or by posting any form of unwanted information about you online.
- Blackmail: This is when someone threatens to harm you or your loved ones by physical means or by sharing real or fake information that may damage reputations (yours or your loved ones’) if you do not do something that they are demanding. The number of people being targeted for this is increasing daily, as some people find it easy to earn money from the anonymity of their screen.
- Cyber Bullying: Cyber bullying is when someone sends you intimidating messages, teases or shames you online. This may also include someone sharing your information publicly online or in a group.
- Trolling: Trolling is when an individual is targeted with harmful and demeaning messages or comments.
- Cyber stalking: It is the repeated use of social networks, mobile communications, and digital forms of technology to harass and stalk you in any way. Cyber stalking can be a one time incident or something that’s been happening for years. It can be by strangers or people close to you.
- Online sexual harassment: Online sexual harassment includes a wide range of sexual misconduct on digital platforms.
- Child Sexual Abuse Material: These can be videos, texts, images, including computer graphics that contain inappropriate sexual material on children.
- Revenge Pornography: Some relationships, as good as they might have been might end up in separate ways due to incompatibility. In a lot of cases where one partner can’t accept the end of a relationship, it might turn toxic. In such cases, which are quite a few, the photographs and videos that you had made in good times and are good memories turn toxic too. The toxic partner will use it to threaten and blackmail in order to gain something, even money for revenge.
- Hacking : Unethical hacking is the unauthorized intrusion into a device or network often used to perform illegal activities or intimidate a target.
- Fake profiles: Impersonating a person, organization or company that may not exist to harass, stalk or gain access to your data.
Cybercrimes are offenses and unethical activities carried out using the Internet, information technology, or devices such as computers and mobile phones, as a tool. Some of the most common violations within cyberspace include hacking, unauthorised publications of photos or online harassment.
Types Of Cybercrimes And Remedies
With the popularity of the internet, instances of scamming and hacking has increased. Scamming is the act of misrepresentation to get sensitive information out of an individual (eg. bank details, private photos, etc.) and hacking refers to gaining unauthorised access to a system or computer. If anyone accesses or assists someone else in accessing your device, or obtains data from it without your authorisation or the authorisation of the person in charge of it, then they may be punished under section 43 and/or section 66 of the IT Act (Information Technology Act). The act of scamming may be punishable under section 66D of the IT Act, sections 308, 318, 319 of the Bharatiya Nyaya Sanhita (BNS), where one may be punished with imprisonment for up to seven years or fine or both. You may also seek compensation from an organisation or company which possesses or handles your sensitive personal information, under section 43A of the IT Act, where you have suffered from misuse of such sensitive data due to the lack of security measures taken by them to protect this.
Oftentimes we find people, especially those in the limelight, being abused on social media. This could be through comments or posts on various sites. Persons posting derogatory remarks on public platforms like Instagram and Facebook may be penalised with imprisonment of up to two years and/or fine, under section 356 BNS. The perpetrator may be made to compensate the victim in addition to the fine, if a civil defamation suit is filed. If one causes annoyance by posting obscene content on social media, by singing, reciting or uttering obscene songs, ballads or words, then under section 296 of the BNS, such person shall be punished with imprisonment up to three months or with fine of up to Rupees thousand or both. Additionally, per section 79 of the BNS, if one posts material or comments on online platforms, with the intention of insulting the modesty of any woman, with the intention that it be heard or seen by such woman, or intrudes upon the privacy of such woman, then such person shall be punished with imprisonment for a term which may extend to three years or with fine or with both.
Online stalking of adults is gender specific offence punishable under Section 78 of the BNS. Any man monitoring the activities of a woman on the internet may be punished under this section with imprisonment for a term which may extend to five years. In case the person stalked is a child, irrespective of the gender of the child and the offender, the same would constitute an offence under S.11 of the Protection of Children from Sexual Offences Act (POCSO Act) and may be punishable with imprisonment for a term which may extend to three years and fine.
As users of social media, some of you may have received indecent messages, videos and texts. Transmitting such indecent images could attract imprisonment for up to 7 years and fine of up to 10 lakh rupees under section 67, 67A and 67B of the IT Act. The offence of showing pornography to a child, sending sexually explicit content of child, etc. are offences as per the POCSO Act and may be punishable with imprisonment for a term which may extend to three years and fine.
The same law applies to instances in which the explicit and indecent digital images being circulated are images of you, irrespective of whether they were obtained without your consent. Publishing and transmitting indecent images in the name of revenge, retribution or vengeance, which is commonly referred to as revenge porn, falls in this category.
Where indecent images or videos of you are recorded or obtained, without your consent, then sections 43, 66 and/or 66E of the IT Act may apply, in addition to the above-mentioned sections. Moreover, any man who watches or captures images of a woman engaging in a private act, where she would usually not have expected anyone to observe her, will be imprisoned for a term which could extend to 7 years and be fined, under section 77 of the BNS.
Publishing morphed or manipulated digital images or videos of you, by a person to whom you had entrusted it, in violation of your trust, may be punished under sections 316 and 351 of the BNS, attracting a penalty of imprisonment which may extend to 3 years or fine or both. If the photos prior to manipulation were obtained without your consent, then punishment may be as per section 351 of the BNS.
If someone is blackmailing you or threatening to publish or circulate your explicit content, irrespective of whether it was obtained with your consent, they may be punished under sections 308 and/or 351 of the BNS, where the act of blackmailing alone may result in imprisonment for a term of up to three years or fine or both.
As far as offences involving inappropriate or obscene content of minors are considered, the act of browsing, seeking, advertising or promoting electronic material depicting children in obscene or indecent or sexually explicit manner, is punishable as per S. 67B of IT Act and may attract imprisonment for up to seven years and fine which may extend to ten lakh rupees. Using a child for pornographic purposes, enticing a child for pornographic purposes, failure to delete pornographic content involving children (even computer-generated artificial content), circulation and storage of pornographic material involving child (including generated images/videos) and possession of the same in some cases are also punishable by the POCSO Act.
Reporting A Crime
On occurrence of any cybercrime, the victim may register a complaint with the nearest cyber cell or the nearest police station. The victim also has the option of registering a complaint with the National Cyber Crime Reporting Portal online, the respective state portals or the option of reporting objectionable content on the respective social media websites or platforms.
Reporting Online
National Cyber Crime Reporting Portal
The victim can report the occurrence of a cybercrime online to the National Cyber Crime Reporting Portal through its website https://cybercrime.gov.in. On accessing the website, if it is a child or gender specific crime, you may click on ‘REPORT WOMEN/CHILD RELATED CRIME’ option and otherwise, you may click on the ‘REPORT OTHER CYBER CRIME’ option on the Menu Bar. If you choose the first option, you will be provided with two further options: ‘REPORT ANONYMOUSLY’ and ‘REPORT AND TRACK’.
However, once a complaint is filed under ‘REPORT WOMEN/ CHILD RELATED CRIME’ it cannot be withdrawn. Complaint filed under ‘REPORT OTHER CYBER CRIME’ section can be withdrawn before it is converted into FIR.
Report Anonymously
If the complainant wishes to remain anonymous, this option may be selected. Here, the victim or the complainant has the option of reporting the crime anonymously by providing details of the incident as well as that of the suspect, if any.
After selecting ‘REPORT ANONYMOUSLY’ click on ‘FILE A COMPLAINT’ option. A dialogue box appears requiring an acknowledgment that the information provided is accurate to the best of your knowledge. On clicking ‘I ACCEPT’, you are giving your acknowledgment that you are aware that providing false information could make you liable to penal actions under the Indian Laws.
Process of registering your complaint:
After clicking on ‘FILE A COMPLAINT’, you will be directed to a page wherein you will be required to give details about the incident as well as the suspect.
Complaint & Incident Details
- Category of complaint: – There are four categories of complaints listed out under this. From the drop-down list, select one of the following:
(1) Child pornography or Child Sexual Abuse Material;
(2) Rape/Gang rape (sexually abuse content);
(3) Publishing or transmitting sexually obscene material in electronic form;
(4) Publishing or transmitting material containing sexual acts in electronic form.
- Date (mandatory) & Time (optional) of the incident.
- In case of delay in reporting the incident, mention the reason for delay (optional).
- State/UT in which the incident occurred.
- District in which the crime was committed.
- If you know the Police Station limits in which you are residing in, mention the jurisdictional Police Station (optional).
- Where did the incident occur? : – From the drop-down list, select the online platform in which the incident occurred. There is a comprehensive list of platforms including email, Facebook, Instagram, Twitter, YouTube, etc. In case of any other website or platform, mention the URL or name of the website or platform. Once you select one of the options, you also need to mention the ID of the offender in the respective platforms or url of websites (mandatory).
- Supporting evidence: – Here, upload photos or screenshots or video giving a clear vision of the offensive content. Choose the file and add.
- Please provide any additional information about the incident – Give a brief description of the events (a maximum of 1500 characters).
- Click on ‘Save and next’.
Suspect Details
This is the next step in filing the complaint. It is an optional page, intended to give leads to the investigating agency. Insert name or photograph or other details of the suspect, if any. However, refrain from giving information if you are unsure about the details of the perpetrator. Click on ‘preview and next’.
Preview & Submit
Assess the preview and confirm that the details entered are accurate. By submitting the complaint, the complainant also acknowledges the fact that providing false information could make him/her liable to penal action under Indian laws. Tick the box next to ‘I Agree’. Confirm and submit.
Once the complaint is submitted online, information will be provided to the jurisdictional police station and a First Information Report will be registered on the basis of the information provided. Thereafter, criminal proceedings will be initiated and continued in the usual manner (more details under ‘Reporting Offline’). However, the complainant will not be able to track the status of his/her complaint submitted anonymously.
Report and Track
In order to track the status of the complaint online, one may opt the alternative option, that is, ‘Report and Track’. If you opt for ‘Report and Track’ you must mandatorily create a User ID with the website, creating a ‘citizen’s profile’, providing personal information including name, title, phone number, email id, date of birth, gender and name of spouse, etc. Once your profile is created, you can report any cybercrime after giving the details of the incident, suspect and that of the complainant. The process of filing the complaint is similar to that described above. Here also, victim anonymity can be maintained if the complaint is made by a person other than the victim. You can check the status of your complaint by logging in to the website.
Report Other Cyber Crime
This option also requires you to mandatorily create a User ID with the website, creating a ‘citizen’s profile’, providing personal information including name, title, phone number, email id, date of birth, gender and name of spouse, etc. Once your profile is created, you can report any cybercrime after giving the details of the incident, suspect and that of the complainant. The process of filing the complaint is similar to that described above. You can check the status of your complaint by logging in to the website and clicking on the ‘CHECK STATUS’ option. You can then enter the complaint ID or search from the request date.
Kerala Police Cyberdome
Similar to the process available at the national level, the victim has the option to report objectionable content on the respective social media platforms, through the website https://cyberdome.kerala.gov.in/reportus.html.
It gives you an opportunity to report through the various media such as Facebook, WhatsApp, Twitter or Email in addition to the option of a direct reporting box in the website which allows you to remain anonymous.
If you choose not to remain anonymous, you may enter your name, email address, phone number as well as your address to supplement your report. This can be submitted by filling out the Captcha code and clicking on a Red Button that says “SUBMIT INFORMATION”
Reporting on the platform
As an alternative option, you may report to the respective social media websites or platforms so as to remove any objectionable content from their page(s). Most social media websites like Facebook, YouTube, Twitter, Instagram, etc. have the option of reporting or flagging the objectionable content(s). The social media platforms may take appropriate action based on the contents reported to them as per their content policy.
Reporting Offline
On occurrence of any cybercrime, the victim may register a complaint with the nearest cyber cell or police station. The reporting procedure is quite similar to that of other crimes.
Go to the nearest police station and give a written complaint detailing the occurrence.
Based on the written complaint, a First Information Report will be registered.
Thereafter, the Police Station shall forward the details to the Cyber Cell, which will take over the investigation.
In the event of a finding that a crime has occurred, the investigating officers may require submission of evidence. It is advisable to retain copies of the evidence that you might submit.
After completion of investigation, depending on the gravity of the offence(s) as well as their punishment, the criminal courts shall take cognizance and initiate criminal proceedings.
Evidence – Types And Safekeeping
A variety of documents may constitute evidence in Cybercrimes. It is important to collect and keep any evidence you may have in relation to your complaint. Among other types of documents, some examples of evidence include copies of emails, chat transcripts, screenshots of the mobile number of the suspect, images, screenshots, videos, url of web pages, etc. The complaint may also be supported and accompanied by physical documentary evidence including printouts, CDs, etc.
You might be required to give the evidence collected to the investigating officer when requested. In such circumstances it is advisable to retain copies of the same.
The sexual exploitation of children is an ever evolving epidemic of child abuse and without proper monitoring, the untethered use of the Internet puts a child at great risk. Internet safety experts warn us almost daily about the sexual exploitation kids are facing today, and child protection agencies can barely keep up with their caseload. In the present scenario, with the ease of use of the Internet, it gives predators an opportunity to get in touch with children they couldn’t reach before and with a sense of anonymity that makes them bold in their approach. The sexual exploitation of children may not be new, but it is a danger that can now reach further into households and schools via the Internet, and all parents and educators must be cautious and prudent about the safety of their children. This is why Internet safety is absolutely imperative for parents and teachers who want to protect their children from sexual predators.
- Talk to your kids about being safe online. Do not shy away or hold information from them. Openly talk to them about the dangers and make them understand that they can trust you to support them in case of a danger or an emergency.
- Do not threaten them or scare them, let them feel safe and understand that they can turn to you in times of crisis.
- Use a child protection software such as NetNanny or K9 Protection to keep your children safe online. (only use these if your kids are under the age of 12. Making use of these beyond that age may harm your relationship with the child.)
- Teach them about what are acceptable and unacceptable conversations online and tell them to talk to you about any person, who they feel is approaching them in a hostile way.
- Make them understand that they do not have to give in to threats no matter what the situation they are in.
- Ask them to never share their personal information online.
- Know what their interests are online and encourage them to use the internet more productively.
- Inform them about dangers of meeting people online and ask them to be open about it if someone is pushing them to meet them outside in secluded areas.
- Ask them not to install unnecessary applications on their phones or desktops. Also inform them not to give permission for random apps to access their Facebook and other accounts.
- Do not upload pictures of children online. Especially those in their school uniforms.
- Do not break their trust. Children too need their space and breaking this repeatedly can cause them to hide information from you and not trust you at crucial times.
- Ask them to keep a safety app handy.
The number of children getting addicted to pornography is increasing. Children observe and watch what you do. If you don’t delete information from your mobiles and sites that you don’t want them to watch before you give them gadgets to use, you put them in danger of watching and imitating what you don’t want them to see. The age group of children trying out what they see on pornography sites is decreasing, so do take care of what is on your gadgets before you hand it over to them
How It Affects Children
- It shapes sexual values, attitudes and behaviors.
- Violent porn creates false ideas about healthy sexuality and intimacy or the development of deep personal relationships.
- Change in expectations in a relationship, physical appearance and behavior.
- Prematurely sexualizes children.
DO’s Never post your future plans, information that reveals your location through GPS, phone, address, school, relations or anything that will help someone learn about you. • Do share photographs/ videos carefully Share only those photos/videos you are comfortable with anyone seeing. • Do be careful while making video calls and while using disappearing chats No matter what people tell you, chats and calls can be recorded and retrieved. • Do save texts for evidence Block out sexually suggestive messages or chats from unwanted people. Do not delete or deactivate accounts or texts. Back up information for proof. • Do be careful while giving your phone to children Parents should be aware of what children are browsing and also make sure that they don’t access adult material available on your phone. • Do be careful when playing games online Don’t reveal your details including number or personal ID online. Don’t make friends through online games. • Do use a strong password Eg: Take a line out of a book, replace words with numbers where possible ( 0 instead of O , 3 instead of E etc.). • Do be careful about downloading applications Spend some time reading the permissions and terms and conditions of the app. • Do learn to switch off If you feel that your gadgets are taking over your life, switch off your gadgets and look for other options like arts, reading a book, listening to music, connecting with nature etc. • Do reach out Reach out to friends, family or the law enforcement agencies like the police if in trouble. Never give into threats, it only gets worse. | DON’T’s Do not leave your phone with friends or at repair shops. Remove the SIM, SD card and reset before giving it for repair. If you can’t do this, stay with the phone while it gets repaired at authorized service shops only. • Do not share photographs of children online Internet is not a safe place to post photographs of children, their photos can be sold online to paedophiles and sex traffickers. • Do not bully anyone online Bullying people online is illegal. It could also lead them to taking their lives. • Do not give into threats or blackmailing The person hiding behind a gadget and trying to scare you is a coward. Break the cycle of fear. Warn them that you will report them to the law enforcement if they don’t stop harassing you. • Do not share/ watch child sexual abuse materials Creating, sharing or watching child sexual abuse materials is an offence • Do not spend time online when you are depressed When depressed, looking at other people’s seemingly exciting lives could leave you even more depressed. • Do not look up social media profiles of people you have broken up with It could lead to mood swings, depression and finding ourselves unable to move on. • Do not share information blindly Do not share without checking if it is genuine or verified, as in a lot of cases it turns out to be fake or false and will mislead others. • Do not use pirated software If you want free software search for open source software. • Do not share posts or messages that incite hatred. It causes issues and induces negativity within you. |
- Stay calm and not panic.
- Do not give in to threats; do not do what they want or meet them. The offenders usually do not go ahead with their claims as they know they are in in wrong and will be in trouble.
- Make records of all communication and save and keep a backup. You will need this in case you need to take further action.
- DO NOT delete or deactivate your accounts or apps. This may cause you to lose critical information.
- Reach out to a trusted person like a friend, colleague or spouse or the law enforcement. When you reach out, you are breaking the circle of fear the predator has built around you to connect you to them. If you can’t get adequate support, please call our helpline at +91- 8891320005
- Tell the offender strongly to back off or let them know that you are not interested in further communications. Also inform them that you will go ahead with legal remedies if they keep bothering you.
- Make sure that the offender knows that you are not scared to go to the authorities if that is what it takes. Offenders depend on you being too scared to go to another person. That is why they use it as their hold over you. Your fear.
- If the threats continue, file a complaint with the local police and take support of family and friends.
- Communicate with your child about the issue. Calm them down and make them understand that you will stand with them and solve the issue. They should know that they are not alone.
- Do not get angry or blame the child for the mistake. Be supportive and make them feel safe.
- Ask the child for details and help them save all the communications and other information from the offender.
- Do not ask the child to deactivate or delete the account as this can cause other undesirable reactions including losing information about the offender.
- Reach out for support in case you need help.
- Take the issue to the law enforcement.
- The most important part is that the child feels safe and that he or she feels confident that you will stand with them.
Introduction
The World Health Organisation recently included gaming disorder in their most recent definition of the international classification of disease. Gaming disorder is characterised by a pattern of persistent gaming behaviour (digital gaming or video gaming), which may be online or offline, manifested by an impaired control of the game.
Video game addiction is very common in India. People often forget daily life activities and can continue to be in the digital world for over 12 hours per day. Video-game addiction is often not realised by the person who suffers from it. What started out as humans controlling devices has now turned the other way round.
Effects of Video game addiction
- Unwanted and uncontrolled interference with daily life activities.
- Impairment of social, family, educational, occupational and other important areas of functioning.
- Use of strategies which traps the users and forces them to use the gaming platforms until they have finished the battles, thereby keeping them addicted to their devices.
- The experiences put forward by the real world cannot compete with the number of dopamine hits the virtual world offers.
- Decline in level of empathy in the society
Signs of video game addiction
The following are some of the emotional symptoms of video game addiction:
- One feels restless or irritated when they are not able to play the particular video game.
- Preoccupied with the thought of the game previously played or anticipating when one can play the game next.
- When asked about the time spent on video games, one lies about it.
- Secluding oneself from people in order to get more time to spend on video games
It is pertinent to understand some of the physical signs of video game addiction, which is as follows:
- Fatigue.
- Migraines due to long hours spent playing video games.
- Strain on eyes which may even lead to permanent eye damage.
- Carpal tunnel syndrome due to overuse of gaming controls or computer mouse.
- Poor personal hygiene.
Video game addiction can have an overall negative impact on the person suffering from it. They may skip meals or avoid sleeping properly for the sake of video games.
Breaking the addiction
To help one get out of video game addiction, it is important for the government, society and most importantly, the individual, to take necessary steps.
- Reduce the amount of time spent on video games. Work out a schedule, and ensure that you follow this religiously
- Seek help from family and friends. They could put targets for you to achieve and remind you to stick to your goals.
- Find new hobbies or activities to replace video games. You can start reading an interesting novel you have been waiting to get your hands on, or explore your inner artist or writer.
- Try a digital detox by staying away from video games for sometime. But always remember that an idle mind is the devil’s workshop. So keep engaging yourself in different activities. Identify your passion and work towards mastering it.



